Researchers Uncover Malicious NPM Packages Stealing Data from Apps and Web Forms
5 de julho de 2022A widespread software supply chain attack targets package manager NPM by December 2021 with rogue modules designed to steal data entered
A widespread software supply chain attack has targeted the NPM package manager at least since December 2021 with rogue modules designed to steal data entered in forms by users on websites that include them.
The coordinated attack, dubbed IconBurst by ReversingLabs, involves no fewer than two dozen NPM packages that include obfuscated JavaScript, which comes with malicious code to harvest sensitive data from forms embedded downstream mobile applications and websites.
“These clearly malicious attacks relied on typo-squatting, a technique in which attackers offer up packages via public repositories with names that are similar to — or common misspellings of — legitimate packages,” security researcher Karlo Zanki said in a Tuesday report. “Attackers impersonated high-traffic NPM modules like umbrellajs and packages published by ionic.io.”
The packages in question, most of which were published in the last months, have been collectively downloaded more than 27,000 times to date. Worse, a majority of the modules continue to be available for download from the repository.
Some of the most download malicious modules are listed below –
– icon-package (17,774)
– ionicio (3,724)
– ajax-libs (2,440)
– footericon (1,903)
– umbrellaks (686)
– ajax-library (530)
– pack-icons (468)
– icons-package (380)
– swiper-bundle (185), and
– icons-packages (170)
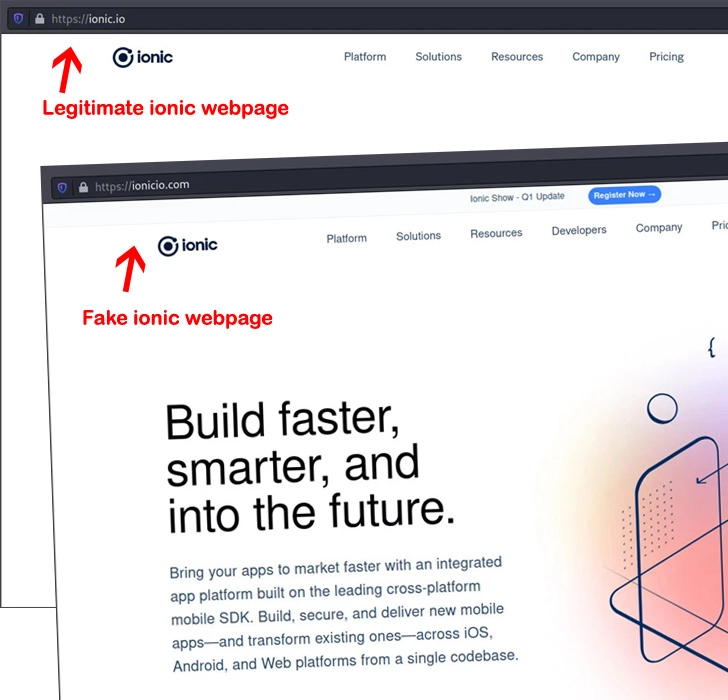
In one instance observed by ReversingLabs, data exfiltrated by icon-package was routed to a domain named ionicio[.]com, a lookalike page engineered to resemble the legitimate ionic[.]io website.
The malware authors behind the campaign further switched up their tactics in recent months to gather information from every form element on the web page, indicating an aggressive approach to data harvesting.
“The decentralized and modular nature of application development means that applications and services are only as strong as their least secure component,” Zanki noted. “The success of this attack […] underscores the freewheeling nature of application development, and the low barriers to malicious or even vulnerable code entering sensitive applications and IT environments.”
Source: The Hacker News
Facial recognition for travel and onboarding top this week’s biometrics and digital ID news

