17-Year-Old Critical ‘Wormable’ RCE Vulnerability Impacts Windows DNS Servers
15 de julho de 2020Cybersecurity researchers today disclosed a new highly critical “wormable” vulnerability—carrying a severity score of 10 out of 10 on the CVSS scale—affecting Windows Server versions 2003 to 2019
The 17-year-old remote code execution flaw (CVE-2020-1350), dubbed ‘SigRed’ by Check Point, could allow an unauthenticated, remote attacker to gain domain administrator privileges over targeted servers and seize complete control of an organization’s IT infrastructure.
A threat actor can exploit SigRed vulnerability by sending crafted malicious DNS queries to a Windows DNS server and achieve arbitrary code execution, enabling the hacker to intercept and manipulate users’ emails and network traffic, make services unavailable, harvest users’ credentials and much more.
In a detailed report shared with The Hacker News, the Check Point researcher Sagi Tzadik confirmed that the flaw is wormable in nature, allowing attackers to launch an attack that can spread from one vulnerable computer to another without any human interaction.
“A single exploit can start a chain reaction that allows attacks to spread from vulnerable machine to vulnerable machine without requiring any human interaction,” the researcher said.
“This means that a single compromised machine could be a ‘super spreader,’ enabling the attack to spread throughout an organization’s network within minutes of the first exploit.”
After the cybersecurity firm responsibly disclosed its findings to Microsoft, the Windows maker prepared a patch for the vulnerability and began rolling it out starting today as part of its July Patch Tuesday, which also includes security updates for 122 other vulnerabilities, with a total 18 flaws listed as critical, and 105 as important in severity.
Microsoft said it found no evidence to show that the bug has been actively exploited by attackers, and advised users to install the patches immediately.
“Windows DNS Server is a core networking component. While this vulnerability is not currently known to be used in active attacks, it is essential that customers apply Windows updates to address this vulnerability as soon as possible,” Microsoft said.
Crafting Malicious DNS Responses
Stating that the objective was to identify a vulnerability that would let an unauthenticated attacker compromise a Windows Domain environment, Check Point researchers said they focused on Windows DNS, specifically taking a closer look at how a DNS server parses an incoming query or a response for a forwarded query.
A forwarded query happens when a DNS server cannot resolve the IP address for a given domain name (e.g., www.google.com), resulting in the query being forwarded to an authoritative DNS name server (NS).
To exploit this architecture, SigRed involves configuring a domain’s (“deadbeef.fun”) NS resource records to point to a malicious name server (“ns1.41414141.club”), and querying the target DNS server for the domain in order to have the latter parse responses from the name server for all subsequent queries related to the domain or its subdomains.
With this setup in place, an attacker can trigger an integer overflow flaw in the function that parses incoming responses for forwarded queries (“dns.exe!SigWireRead”) to send a DNS response that contains a SIG resource record larger than 64KB and induce a “controlled heap-based buffer overflow of roughly 64KB over a small allocated buffer.”
Put differently; the flaw targets the function responsible for allocating memory for the resource record (“RR_AllocateEx”) to generate a result bigger than 65,535 bytes to cause an integer overflow that leads to a much smaller allocation than expected.
But with a single DNS message limited to 512 bytes in UDP (or 4,096 bytes if the server supports extension mechanisms) and 65,535 bytes in TCP, the researchers found that a SIG response with a lengthy signature alone wasn’t enough to trigger the vulnerability.
To achieve this, the attack cleverly takes advantage of DNS name compression in DNS responses to create a buffer overflow using the aforementioned technique to increase the allocation’s size by a significant amount.
Remote Exploitation of the Flaw on Windows
That’s not all. SigRed can be triggered remotely via a browser in limited scenarios (e.g., Internet Explorer and non-Chromium based Microsoft Edge browsers).
Allowing an attacker to abuse Windows DNS servers’ support for connection reuse and query pipelining features to “smuggle” a DNS query inside an HTTP request payload to a target DNS server upon visiting a website under their control.
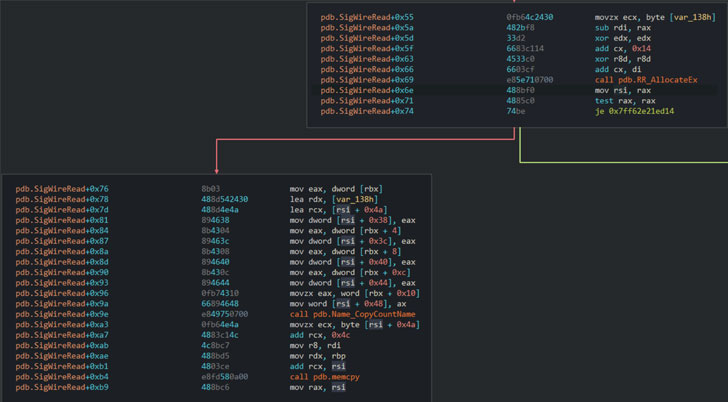
What’s more, the bug can be further exploited to leak memory addresses by corrupting the metadata of a DNS resource record and even achieve write-what-where capabilities, allowing an adversary to hijack the execution flow and cause it to execute unintended instructions.
Surprisingly, DNS clients (“dnsapi.dll”) are not susceptible to the same bug, leading the researchers to suspect that “Microsoft manages two completely different code bases for the DNS server and the DNS client, and does not synchronize bug patches between them.”
Given the severity of the vulnerability and the high chances of active exploitation, it’s recommended that users patch their affected Windows DNS Servers to mitigate the risk.
As a temporary workaround, the maximum length of a DNS message (over TCP) can be set to “0xFF00” to eliminate the chances of a buffer overflow:
reg add “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters” /v “TcpReceivePacketSize” /t REG_DWORD /d 0xFF00 /f
net stop DNS && net start DNS
“A DNS server breach is a very serious thing. Most of the time, it puts the attacker just one inch away from breaching the entire organization. There are only a handful of these vulnerability types ever released,” Check Point’s Omri Herscovici told The Hacker News.
“Every organization, big or small using Microsoft infrastructure is at major security risk, if left unpatched. The risk would be a complete breach of the entire corporate network.”
Source: The Hackers News
Performance Improvements via Formally-Verified Cryptography in Firefox
14 Tech Pros Predict The Next Big Thing in Cybersecurity And Encryption
Online Identity Is Important: Let’s Upgrade Extended Validation. By Patrick Nohe

