Cloud environments introduce a variety of security challenges to organisations and their chief information security officers
Huge numbers of large and small organisations are moving away from traditional, on-premise IT environments to cloud-based platforms.
This move creates many new opportunities to improve business efficiency and effectiveness, but also introduces security threats such as data breaches, unauthorised access and complicated identity management.
What is the trend?
Increasingly more companies now use cloud environments for service models such as infrastructure as a service (IaaS), platform as a service (PaaS) and software as a service (SaaS). These enable the use of virtual machines, storage, load balancers, execution runtime, databases, web servers and applications provided and hosted by third parties. Many of which are in large data-centre hubs in locations such as London, Paris, Amsterdam, Frankfurt and Dublin.
“As of 2021, around 50 percent of all corporate data is stored in the cloud. This share reached 30 percent in 2015 and has continued to grow as companies increasingly shift their resources into cloud environments in the hope of improving security and reliability next to advancing business agility.” Statista
The characteristics of cloud environments, and service models for them, are summarised in the diagram below from the Cloud Security Alliance (Security Guidance for Critical Areas of Focus in Cloud Computing v4.0).
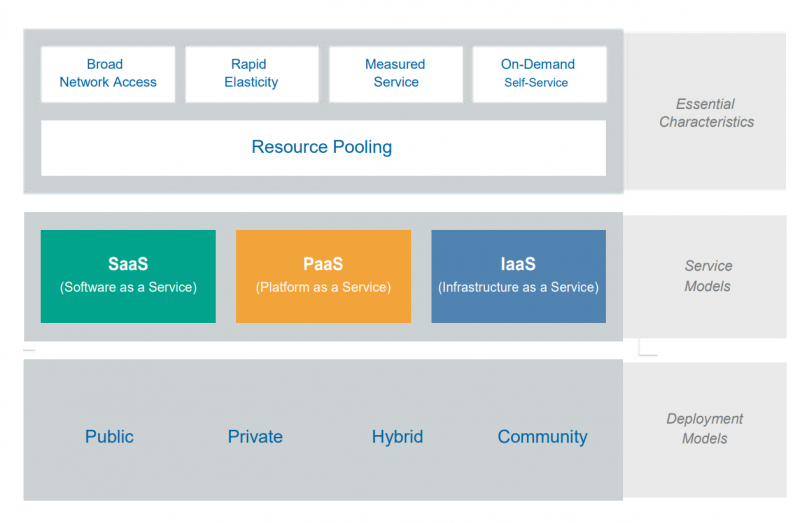
Organisations often use multi-cloud environments when they implement several of the service models illustrated above and store their data at different places – often with a variety of providers.
These providers are partly responsible for the security of their cloud environments and the data held there, and this is drawn up in the service-level agreements created with their clients.
But most of the security concerns still fall within the scope of the client organisation itself. And auditing and controlling these external providers takes time and resources too.
What is the impact on security?
Cloud environments introduce a variety of security challenges to organisations and their chief information security officers. We cover some of the key concerns here.
1. Data breaches
When your data is stored on your premises, your IT department has absolute control over it. They’re fully responsible for it and can see at any time whether there are likely or actual breaches. When you migrate your data to the cloud, the provider of this storage service monitors it for you. So, as an organisation, you start to rely on a third party to take care of your data’s security.
Inevitably, this means you lose some control. And, in recent years, there have been numerous data breaches in the cloud – including some involving high-profile companies such as Yahoo, Alibaba, LinkedIn and Marriot International. Data breaches, amongst other cloud-based security threats, can result in loss of sensitive data, reputational damage and fines in relation to regulations such as the GDPR.
2. Unauthorised access
It’s much harder to safeguard data from external threats and unauthorised access when it’s in a cloud environment than when it’s stored on your premises. And, as cloud providers tend to store data for multiple organisations, it makes them prime targets for hackers. Shifting your applications and data to the cloud can expose them to easier access from unwanted parties, as you have to rely on the cloud provider to handle access management.
3. Identity management
To enable employees and systems to work securely with data, applications or infrastructure in the cloud, they need to be identified properly. This means the cloud environment, and the organisation hosting it, need to know who or what is trying to access the environment and if they are allowed to do so. But how do you identify who is allowed access? And how do you manage all of this? That’s where digital certificates come in.
The importance of using digital X.509 certificates in the cloud
To mitigate the security threats that come with cloud environments, you can use carefully managed X.509 digital certificates. X.509 is a standard that defines the format of digital certificates used in many internet protocols (such TLS/SSL) for securely browsing the web. These certificates are tied to a key pair that, together, enable cryptographic operations such as secure access or data encryption. They’re commonly used to enable people or machines to securely authenticate themselves when accessing an environment, or to encrypt data that’s being stored or transmitted.
Digital X.509 certificates can be used to:
- Encrypt data being stored in the cloud. As stated in the GDPR, data encryption is a technical measure you can use to ensure your data’s confidentiality. Because it means that, even if there is a breach, the data is of no use to the hacker because they can’t decrypt it.
- Set up secure (TLS) connections within a cloud environment or between environments at different locations or providers.
- Maintain data confidentiality during transit by preventing it being read or leaked by unauthorised parties.
Moreover, it allows you to ensure that only authorised people or systems can access your cloud environment because it only trusts the certificates issued by your organisation, for example. If an authorised party doesn’t have trusted certificates, it can’t gain access.
“Cloud security, compliance, and the certificates that help support cloud communication have all come a long way.” – DataCenter Knowledge.
In conclusion, by using and managing your own X.509 certificates, you can take back control over your data and access to it – even when it’s moving to or in the cloud.
How can you manage digital certificates?
The strategy outlined above calls for careful use and management of digital certificates and their corresponding key pairs. A certificate management system (CMS) is a secure, efficient way to manage certificates for every person or system authorised to access your cloud environment.
Windows Hello for Business (WhfB), for example, is based on a certificate structure and uses digital certificates to ensure secure access to Azure environments. But the certificates need to be managed well to ensure the right people can use WhfB in the best possible way.
By using a flexible CMS, you can ensure the right policies are followed and the right people or systems get the right digital certificates. A CMS will also help you automate as many of the processes surrounding this as possible. You can even connect a CMS to so-called containers (that include entire software applications with all their dependencies) so you can manage the related digital certificates through a standardised API.
Another advantage of using a CMS is that, as an organisation, you can keep control over your own certificates and keys rather than handing this over to the cloud provider. We call this ‘bring your own key’ (BYOK).
As cloud use will only increase, now is the time to take action and become fully in control. By applying a digital strategy that uses centrally managed digital certificates, you can secure access to your cloud environments and the data your organisation holds there.
Source: AET Europe
CIP Cast – Webinar IoT – Phil Zimmermann and Ben van Lier
Philip R. Zimmermann apresenta o 3º episódio AET Security Topics: Quantum Key Distribution
Philip R. Zimmermann apresenta o 2º episódio AET Security Topics: Secure Enclaves
INTERNATIONAL NEWS
Crypto ID publishes international articles about information security, digital transformation, cyber security, encryption and related topics.
Please check here!


