How easy it is to spoof or imitate a “safe” SSL site
All website owners are being continually encouraged to switch to SSL ( HTTPS) to secure their websites and prevent “bad thing happening”. Lets get a few things straight immediately.
An SSL certificate is NOT proof of a site being good, honest, legitimate, free of malware, safe to use or that it actually is what it says it is. All that a standard SSL certificate proves is that the connection between you and the website is secure and cannot ( easily) be intercepted and data you send over the net to that site will get to the site and not elsewhere.
What it does do is allows you to connect safely, make comments and know that any information that you need to submit to make the comment, like a name or email address is safe and won’t be intercepted on the way to the site.
There is another type of SSl certificate called an EV certificate ( extended Validation). These cost a lot more than standard SSl certificates because they do prove that the website is who or what is says it is. They go through a whole range of checks and are only issued to legitimate companies, organisations, charities and Government Departments who are able to completely prove the identity of the site in question and the entity owning or running the site.
I recently read a blog post by the renowned security expert Troy Hunt, who has added an EV certificate to his ” Have I been Pwned ” website This site lists many website breeches where users details have been leaked.
As Troy says:
Trust is a really difficult thing to define. Think about it in the web security context – how do you “trust” a site? Many people would argue that trust decisions are made on the familiarity you have with the brand, you know, brands like LinkedIn, Dropbox, Adobe… who’ve all had really serious data breaches. Others will look for the padlock in the address bar and imply by its presence that the site is trustworthy… without realising that it makes no guarantees about the security profile of the services sitting behind it. Then there’s the security seals placed on the page and, well, just go and read clubbing seals if you’re not already aware of just how fundamentally irrelevant (and even dangerous) they are.
We see so many phishing and malware sites set up that spoof or imitate well known sites, often Government or banking /credit card /finance sites. All these site generally have a SSL certificate and some will go to the extent of using an EV certificate. However the majority will just use a standard SSL certificate thinking that the user sees the padlock in the browser bar, knows it is safe ( it isn’t) and merrily goes on its way saying ” Use me I am the safest site on the net”
We need to educate and spread the word that the only guaranteed “safe” or “Identified” website is one with the green URL bar and an EV certificate proving the identity of the site owner.
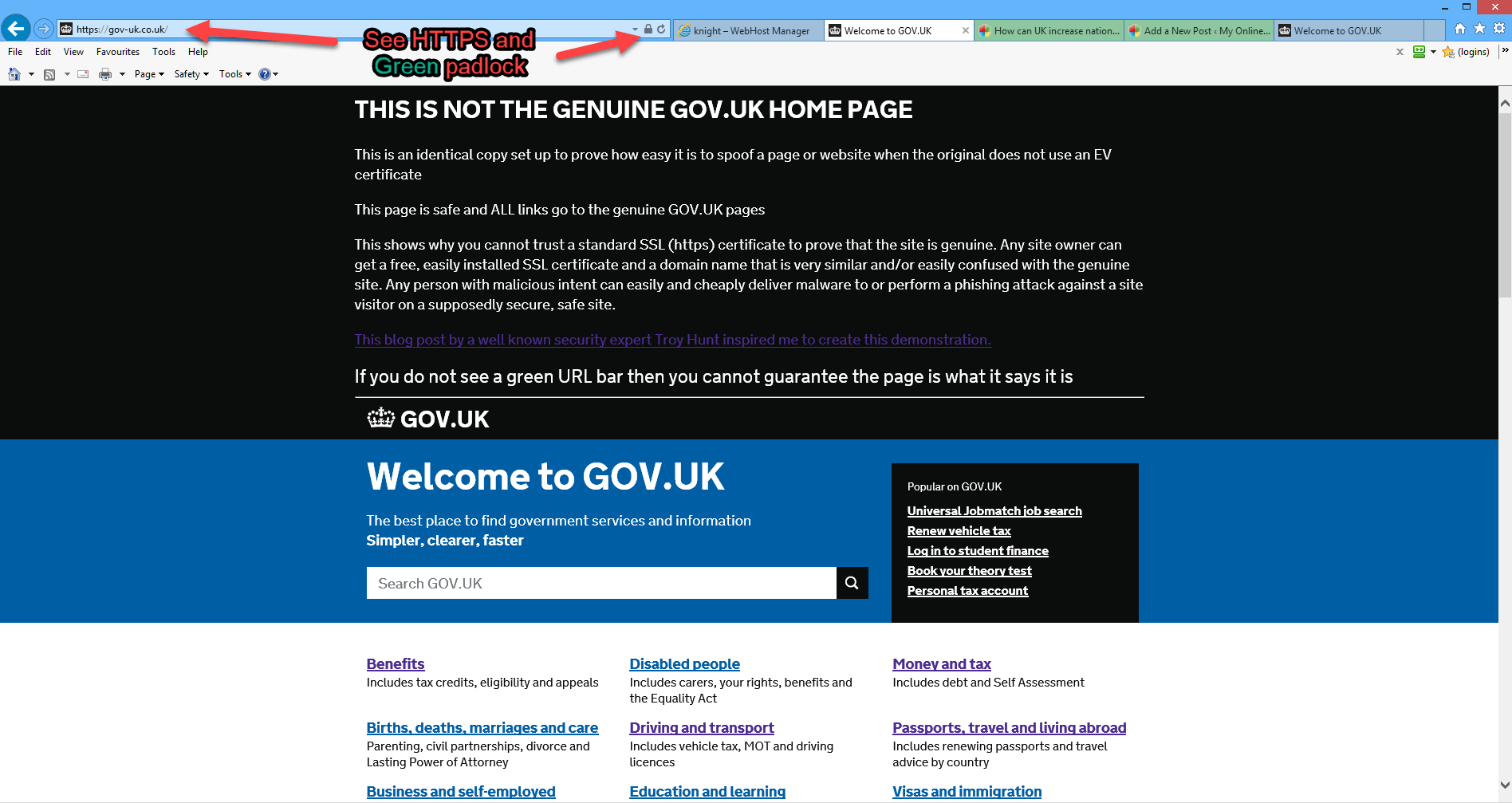
I decided to prove how easy it is to set up a fake site spoofing the UK Government gateway https://www.gov.uk/ I purchased a similar domain name gov-uk.co.uk/ which is a completely believable domain that is so similar to the real one, that anybody can be fooled by it. Stuck a free SSL certificate on it, changed DNS to point to a folder on an existing domain on my server & uploaded a slightly altered copy of the genuine GOV.UK website.
Almost anybody visiting my spoofed site https://gov-uk.co.uk/ ( if I had not put a big warning at the top of the page) would think it was the genuine GOV.UK site
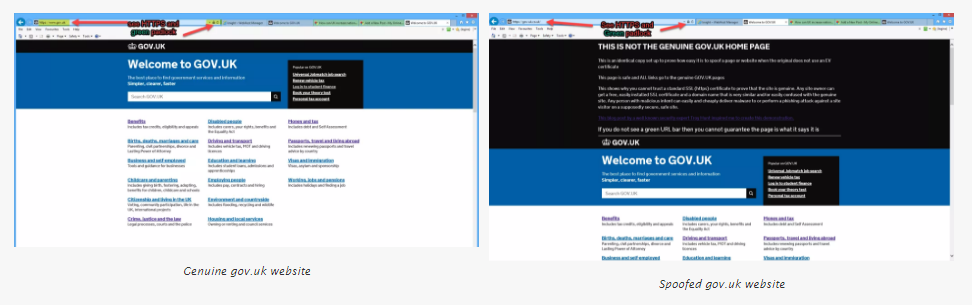
Could you tell the difference? especially if you visited the site from an email link like this HMRC malware delivery attempt. Just imagine if the malware gang had put up a copy of the site with any links you click actually downloading the malware file instead of attaching it to the email. Yes, if you are a paranoid security professional, wearing a tinfoil hat all the time, who examines each and every SSL certificate before doing anything on the website, you can see the difference, but how many “normal people do that ” I could have easily made a new account on my server so the SSl certificate would have read issued to “gov-uk.co.uk instead of to: gov-uk.thespykiller.co.uk but that would have taken a bit longer to set up and I wanted to do this as quickly as possible, in the same way that a phisher or malware spreader would do.
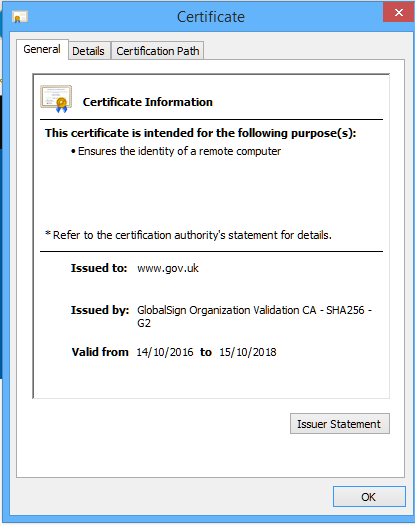
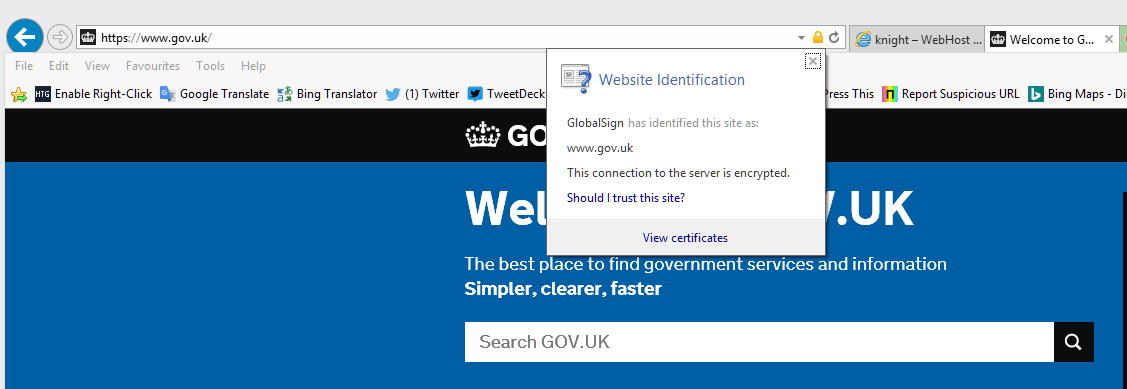
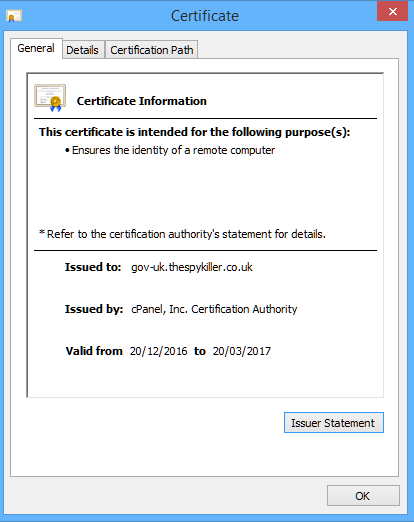
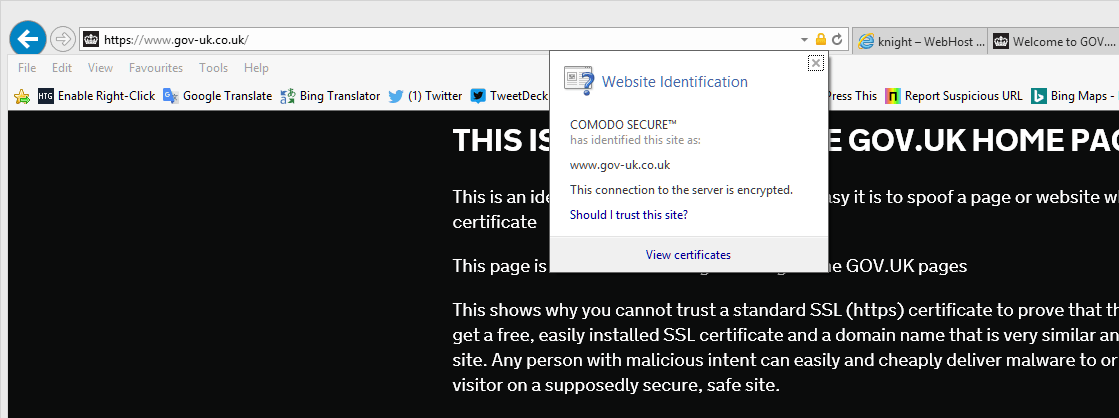
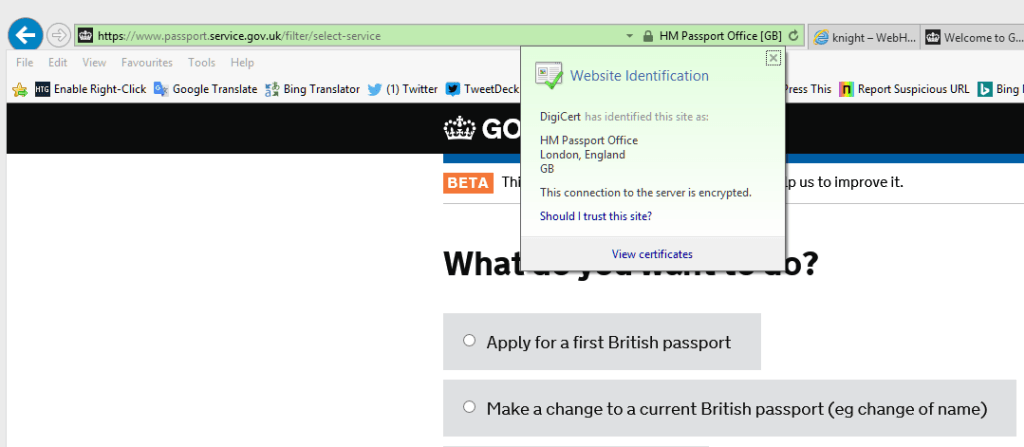
Now if you look at a UK government site that does have an EV certificate you easily see the difference and how much harder it is to spoof or imitate the site. You see the URL bar is green. Click on the padlock and you see clearly identified as HM Passport Office London. I just cannot understand why gov.uk only has EV certificates on a few subdomains of the gov.uk gateway site. Why don’t they use a single EV certificate to validate the entire gov.uk domain. A green identity pop up when selecting the padlock saying ” identified as: UK Government London” would be much easier to maintain and avoid certificate errors and mismatches, especially when the Government department changes its name in the next reshuffle. They seem to think that only sites that YOU input information or make payments through need an EV certificate. My view is that ANY part of the site that gives important information or allows you to download forms etc also needs an EV certificate, to completely eliminate the possibly of a spoof/fake site being used. This, in reality means the entire site needs an EV certificate.
The same applies to many Banks and financial bodies. The home page is often an unsecured HTTP site. For example TESCO bank make it easy to spoof themselves. The home page is http://www.tescobank.com/ and you only get sent to a secure validated page on selecting login https://www.tescobank.com/sss/auth That makes it trivially easy for a scammer/phisher or other fraudster to imitate the Tesco bank home page with a similar domain and steal information.

O CryptoID publica artigos em outros idiomas na coluna International News
Please read our articles published in other languages at International News

