CYBER WAR
by Deivison Pinheiro Franco*

Deivison Pinheiro Franco | Colunista do Crypto ID
The cybernetic sector contemplates the use of technological means destined to the transit of information, even those dedicated to strategic sectors, and to protect them is fundamental for the maintenance of the stability and security of the society, since we live in the information age, in which The dependence on technology increases every day and the risks inherent in the lack of security grow exponentially.
In this way, cybersecurity and security emerge as knowledge of extreme relevance not only in computer science, but also in the military and intelligence areas, which are usually in charge of the protection and defense of a nation.
In this context the actions of Cyber Security are essential, since it is through them that incident response and intrusion detection services are implemented, along with content verification and forensic computing, which is responsible for the analysis of all traces and records Related to an incident, enabling the preservation, collection, processing and analysis of cybernetic traces.
What you will learn
- What is Cyber War
- The Cyber War Causes and Impacts
- The Principles of Cyber Intelligence and Cyber Defense
What you should know
- Basics of Information Security
- Basics of Cyber Strategy
- Basics of Cyber Space Structure
On June 14, 2016, NATO (North Atlantic Treaty Organization), through its Secretary General, Jens Stoltenberg, classified cyberspace as an official operational domain of war. With this classification, there are now 4 domains of war: land, sea, air and cyberspace. In this context, where threats and defenses coexist, nations react to protect their infrastructure and population. The states, seeking to protect their interests in cyberspace and with their thinking also focused on National Defense, place their actions in three types of visions: political, strategic and tactical or operational. The political vision is focused exclusively on the area of Security, the strategic vision is focused on Defense and the tactical vision is geared towards the Cyber War.
On this way, this article will help you understand what Cyber War is, how it can impact your life or business on a personal level, and explore the national aspect from both the policy and practical levels. It will take you from the strategic through to the tactical level explaining the people, methods, virtual battlefield framework, tools, trends, impacts, and way ahead.
The Cyber War Definition
A definition of Cyber War is not easy. In fact definitions for Cyber War or Warfare are both under debate. We will start with a simple definition of Cyber or Cyberspace.
The world has been experiencing successive technological and conceptual changes, be they good or bad, in which nations with security and cyber defense techniques begin to act in virtual space in full form, forming a new mode of combat – what was planned and executed by Means of physical weapons in the four domains of war (earth, sea and air), is now exercised by the confrontation of cybernetic weapons in a fourth area of war – the cybernetics. In this new area, attacks and reprisals are carried out with the aim of delaying development and compromising the strategic structures of enemy nations.
Cyber War is defined by an action or associated set of actions using computers or computer networks to carry out a war in cyberspace, or by withdrawing from operation Internet services and / or normal use of the population (energy, water, etc.). ) Or by spreading malicious code over the network (viruses, trojans, worms, etc.). This concept, to be better understood, has to be analyzed in parts. It follows, therefore, that a cyber attack can be practiced by an individual, or by a group of individuals, or by a specific organization or by a State, using only one machine or set of machines, remote or not, but having a Specific purpose; Attacks can be planned and executed from a defined location or through a network of remotely executed computers; The action taken by the criminals is aimed at removing a certain site and / or service from Internet providers, and may also reach the so-called critical infrastructures of a region and / or country and result in catastrophic and immeasurable results when, for example, provoking A collapse in the power transmission network, causing blackout and / or delaying the return of the service.
The subject of Cyber Warfare is therefore quite comprehensive. It only affects circumstances in the real world, including the threat to the sovereignty of a country that, together with the technology and constant evolutions of the data and voice traffic mechanisms, would tend to evolve and improve protection mechanisms. In other words, once the threat to sovereignty occurs the logical tendency is to create defense mechanisms and reaction, if necessary. However, it is not what is observed. Like the public sectors, the private sector also suffers the effects of this war and industrial espionage, increasingly carried out through technological means, as it is done with less risk and an acceptable operating cost.
In this way, offensive techniques are used to target targeted cyber attacks, which may be in conjunction with physical military operations, which is why the subject has been treated with special attention by several countries, given the destructive power that this new modality of war may have , And especially for economic damage if the attack is successfully carried out on critical infrastructures and sensitive points such as electric power grids, nuclear power plants, water sources, and even the transportation system of a nation. Officially proves the existence of cyber wars, however, there are signs that point to the involvement of nations in attacks that have become famous, such as in Estonia in 2007, in North Korea in 2008 and in Iran in 2010. The latter, STUXNET, became known due to the use of what was called “the first guided cyber missile”, whose purpose was to damage the Iranian nuclear program.
The Cyber war Context
With the advancement of Cyber War and the increase of its potentially damaging potential, there is a risk that the response to an attack will no longer be just “virtual” and will use conventional means of warfare. In 2011, the United States reported that it could retaliate against a cyber attack just as it would counter any other type of threat, including the use of military force and the application of economic sanctions. In 2015, this position was ratified with the publication of a measure that authorized the blocking of assets of persons involved in cybercrime.
As a consequence of this new modality of combat, it is imperative that countries develop the knowledge to apply security and cyber defense policies in an effective way, aiming not only to create an army of cyber attack but, mainly, to defend their critical infrastructures. In view of this, there are already tools to monitor cyber attacks and other threats, in which it is possible to monitor in real time who is attacking who, where and to where an attack is being directed and where (means of transmission, communication ports , Protocols, etc.). These tools also display some detailed features, including the world map, about their peculiarities, also showing a macro / micro perspective / perspective of a desired scenario. Among these tools we can mention three very interesting and that give this vision of cyber attacks throughout the world:
1) Digital Attack Map[1]: a tool that displays proliferated anonymous DDoS attacks from all the origins of the world;
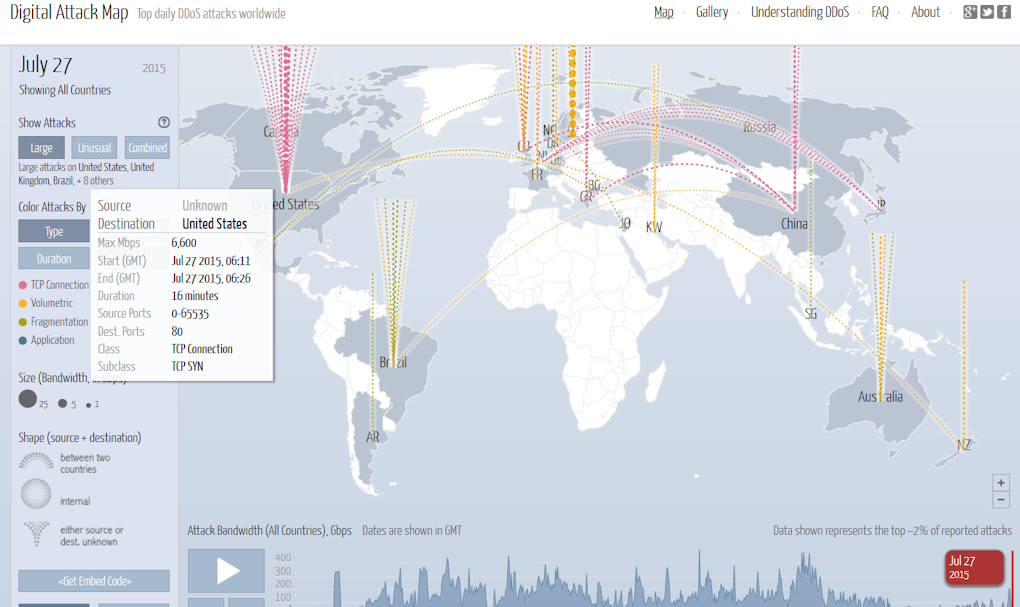
Figure 1. Digital Attack Map Screen.
2) Live Norse Attack Map[2]: a security solution developed with a focus on cyber attacks, whose main objective is to proactively monitor attacks by identifying and classifying their risks;
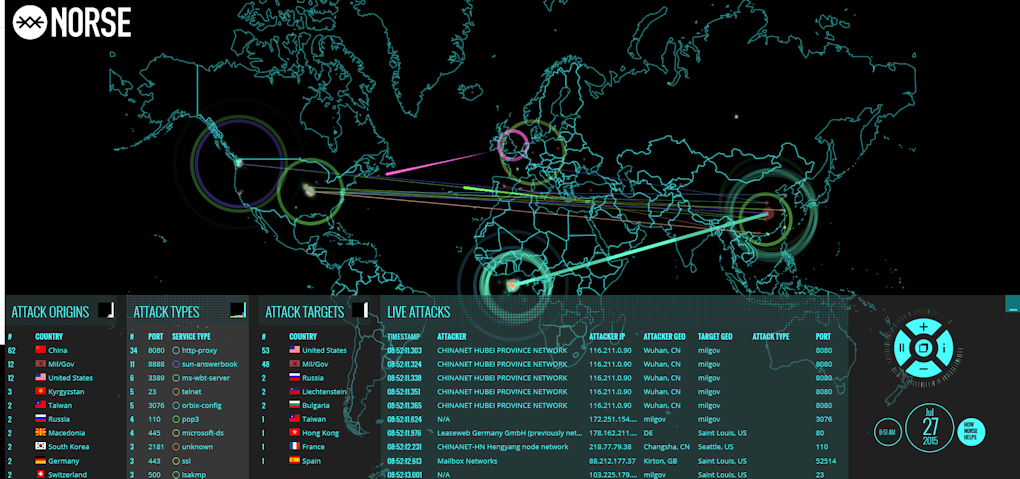
Figure 2. Live Norse Attack Map Screen.
3) Kaspersky Lab’s Cyberthreat Real-Time Map[3]: an interactive cybermap, by Kaspersky, that allows you to visualize different types of threats and the ways in which they are distributed;
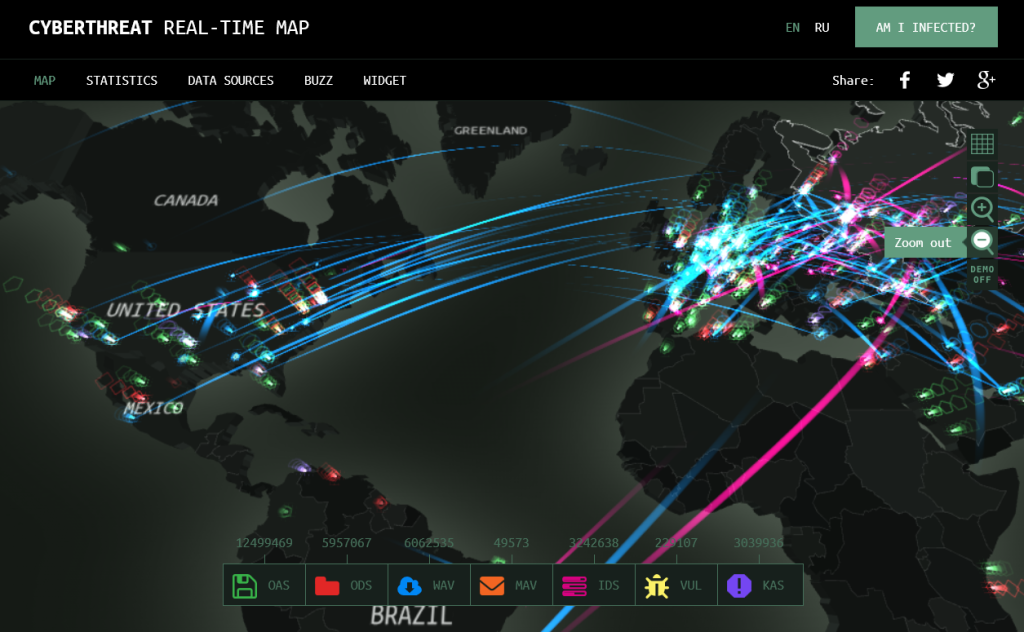
Figure 3. Kaspersky Lab’s Cyberthreat Real-Time Map Screen.
4) Fortinet Threat Map[4]: the Fortinet graphic interface tool that shows remote execution attacks, memory related attacks, remote location attacks, DoS attacks etc;
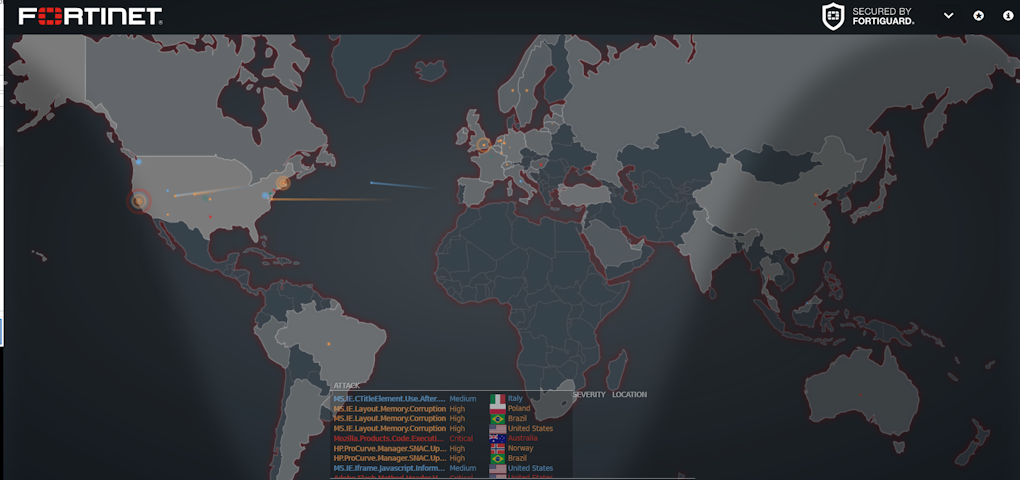
Figure 4. Fortinet Threat Map Screen.
5) Fireeye Cyberthreat Map[5]: a Fireeye tool based on a subset of real attack data, which is optimized for better visual presentation.
Figure 5. Fireeye Cyberthreat Map Screen.
The Cyber Weapons
Cyber Weapons are the weapons that we likely envision when discussing Cyber War. These are the set of tools that is used to conduct reconnaissance, scout out the networks and systems of our opponents, and attack the various targets we might find.
When we look at the use of such tools in a Cyber War context, we might ask how they are different than the tools used in every day penetration testing of applications, systems, and networks. The answer to this is that, in many cases, they not conceptually different to any great degree, but the scope of their use is greatly increased in a Cyber War scenario.
Where penetration testers may be bound, contractually in some cases, to shy away from the tools or settings in tools that are labeled “dangerous” due to their possible deleterious effects on the target at the other end, such effects may be acceptable, or even desirable in a cyber conflict. This may not always be the case, and we certainly may still want to be stealthy and cautious in some scenarios, but this opens up the use of the common tools in such a way that we do not normally see in penetration testing outside of a lab environment.
Another common question that arises in discussions of tools that might be used during Cyber War is that of “secret” military or government tools. There are always rumors of gigantic military botnets that are a billion nodes strong, or tools that can cut through encryption like butter. As we have yet to see a no holds barred Cyber War publicly erupt, the good answer to this question is that although such tools almost certainly exist, we will not know the specifics regarding them until they are brought out of hiding and publicly deployed.
Given past examples of military weapons that were held in extreme secrecy, such as the Manhattan Project and the Stealth Fighter, we would certainly be rash to assume that similar projects do not exist for cyber weaponry, or that super-skilled hackers are not being trained in the bowels of the National Security Agency (NSA). However, from the examples that we can see publicly, government and military cyber warriors are going through the same training, in many areas, and using many of the same tools as their counterparts in the civilian world.
In the case of individuals, corporations, hacktivists, criminal organizations, and other non-state actors, we are more likely to see the use of common or custom developed tools. Such groups are often presumed to be the origin of many of the more pervasive items of malware, attack websites, and the source of any number of small scale cyber attacks. As such, they are on a good footing to participate in Cyber War on a larger scale, and certainly can be considered a serious threat.
When we discuss the broad categories of tools: reconnaissance, scanning, infrastructure, application, and operating system, we might also consider the sources of such tools. A very large portion of the tools in the arsenal used by Cyber Warriors, penetration testers, hacktivists, and terrorists are free and/or open source, and are regularly maintained and enhanced by their base of users. There are also quite a few commercial tools, or tools that are free with commercial components, some of which are very good indeed, but can be quite expensive.
We may very well find commercial tools in the hands of Cyber War forces that are backed by, or in the employ of, nation states, but we are less likely to find them in the hands of individuals or small groups. Nonetheless, in skilled hands, the free tools can be highly effective, if less automated, and are used regularly by a variety of attackers.
“0 DAY” EXPLOITS
Malware is becoming increasingly sophisticated and being used not only by cybercriminals but also by military and intelligence government entities. Stuxnet, Flame and Duqu are examples of these ultra-advanced codes.
Many sources have already stated that such software is, in fact, cyber weapons, designed to collect or destroy information from other countries. Even such malicious code is being developed to be used in a possible cyber war.
But what really differentiates a common, cyber-crime code from a code developed for war purposes?
To begin with we must know that a cyber weapon is a computer code used for the purpose of threatening or causing physical, functional or mental damage to structures, systems or living things. In addition, the Tallinn Cyber War manual states that cybernetic weapons are cybernetic means capable of causing injury or the death of people; Or damage and destruction of objects.
The advanced codes used in Cyber Warfare and Cyber Intelligence have several peculiar characteristics:
- Use of “zero day” exploits to subvert security technologies;
- The attacker has in-depth knowledge of the technologies and systems used by the target;
- Use of techniques to become undetectable and prolong the permanence in compromised systems;
- Use of coordinated attacks for espionage, data theft and cyber sabotage.
Coordination in a cyber attack is very important since, as in a real military operation, errors must be minimized and the target should not suspect that it is under attack. In this way, planning a cybernetic operation is fundamental, unlike a criminal operation that seeks to attack as many targets as possible, and is not relevant if some of these victims are aware that an attack is occurring. In addition, a well-organized cybernetic operation is commonly targeted to a single target or a small set of targets. Already attacks by ordinary criminal organizations do not have this characteristic.
“Zero Day” exploits are extremely effective codes that exploit vulnerabilities that have not yet become public or that do not yet have a fix, and are capable of compromising systems that have high security and updated patch management.
Trade in these vulnerabilities is becoming commonplace and is not currently considered illegal in most countries. However, it is ethically questionable, since vulnerabilities are sold and purchased for military and criminal uses, and the manufacturer of vulnerable software is not informed of such flaws in its products.
Several companies carry out this type marketing: Zero Day Initiative (ZDI)[6], ZERODIUM[7] and Mitnick’s Absolute Zero-Day™ Exploit Exchange[8] are just a few. In addition, governments also carry out the direct purchase of this type of technology, with the United States and China being the most active in this market. These cited companies buy vulnerabilities and exploits from researchers around the world and resell them to governments and private companies.
Considering the dangers of a Zero Day vulnerability, its use in cyber weapons and a trade already established in this area, it is possible to state that the international traffic in cyber weapons is real and is happening at this very moment.
Cyber Intelligence
Cyber defense mechanisms, similar to those in the real world, are considered necessary in the virtual world. For this, the purpose of Cyber Intelligence is to provide the necessary knowledge to defend and optimize the proactive response capacity in case of a cybernetic / ongoing threat. However, threats in the virtual world tend to be more dynamic than real-world threats, which leads to less reaction time on the part of the target being hit. Therefore, intelligence actions, based on specific hardware and software mechanisms, together with human knowledge, can be fundamental for better cyber defense and incident response, causing countries, public and private organizations, to position themselves or not adequately In relation to their digital security.
Suitably or not is to say that countries and / or companies do not always give the real dimension to the problem and, consequently, the response to it. Investments are extremely low, which makes (re) actions restricted, not to say minuscule. It is important to mention that there is no proper distinction between civilian and military targets in an eventual “Cyber War”, which requires constant monitoring and analysis of the factors, since critical infrastructures are exposed to actions, both in the real world and in the virtual world.
Cascade failures can occur when individual vulnerabilities, which may be innocuous or manageable in isolation, but with the potential to initiate domino effects through complex systems interdependent with each other, are attained. For example, a successful attack on the computing apparatus of a domestic port can have a global impact on international trade, energy supply and production, due to the interdependence of the global navigation system. In the same way, a cyber attack on the air traffic control system would not only put lives at risk but threaten to undermine a myriad of economic activities dependent on air transport operations.
So, what are the key factors that should be analyzed? What can help effective advocacy and pro-action? What are the main virtual vulnerabilities? What are the characteristics of malicious code distributed on the web? How it works and what is cyberspace? What is the amount of clandestine financial movement in the virtual world? What are the methods of detecting threats? And finally, who can answer these questions?
As seen, several questions demand response and there is the work of Cyber Intelligence. It serves to guide public and private organizations in monitoring, detecting and analyzing virtual threats, suggesting proactive and comprehensive actions in a constant way, where the maxims are in the response and quick solution.
With this, Cyber Intelligence is nothing more than a process that takes into account the cyberspace, aiming at the obtaining, the analysis and the capacity of production of knowledge based on the virtual threats and with prospective character, sufficient to allow formulations, decisions and actions Of immediate defense and response aimed at the virtual security of a company, organization and / or state.
Concluding this rationale for the subject, Cyber Intelligence can cover:
1. Attacks on public or private networks and web pages.
2. nalysis of vulnerabilities over existing networks, systems and services, focusing on the interweaving to the regional, national and / or global computer network.
3.Constant analysis and monitoring of malicious codes distributed on the web, observing standards, methods and forms of dissemination, such as:
A – Monitoring the external and internal origin of attacks and distribution of malicious code, allowing the demarcation of prevention and / or repression strategies.
B- Intense monitoring of adwares, worms, rootkits, spywares, viruses and trojans, observing behavior, polymorphism, purpose and form of diffusion.
C- More specifically, monitoring the distribution of phishing scams and other malicious code (malware), both by web sites and by email and other forms of dissemination, with special attention to social networks and instant messaging communicators.
4. Focus on social engineering and harmful effects, especially on electronic fraud.
5. Observation and cataloging of digital espionage cases, in addition to checking the services of the species offered commercially via the internet.
6. Detect and monitor data on electronic fraud.
7. Follow-up of technological development for the detection of threats and immediate responses to virtual threats.
8. Proposing contingency policies for cyber-terrorism cases, preparing public and private organizations for existing threats and, in the event of action, seeking to minimize the effects of the incident.
Cyber SECURITY AND CYBER DEFENSE
The concept of cyber security can be explained in several ways, depending on who applies it. However, it is seen by a nation as the art of defending the existence and continuity of information, in an original or processed way, present in virtual space.
The application of cyber security aims to protect information assets and their critical infrastructures, safeguarding the established pillars of information security:
A) Confidentiality: guarantee that information is accessed or manipulated only by authorized entities;
B) Integrity: guarantee that the information is maintained with all its original characteristics, or modified only by authorized parties
C) Availability: guarantee that information is always accessible to those who are entitled, whenever necessary;
D) Authenticity: guarantee that the information comes from the indicated source.
The concept behind cyber security is treated as a state strategy by many nations because of the high technological dependence of its critical infrastructures such as energy, water, transport, finance, telecommunications and defense. Thinking more deeply about this type of concept and its implementation, it can be seen that security is one of the great challenges of this century. The United States asserts that cyber attacks are the greatest threat to its national security, including terrorism.
Cyber security must be present in the daily life of any institution or individual, since it must play a central role in cyberspace, in the form of training and awareness programs, and may be obligatory depending on the function performed by the user. Although it is an issue already addressed by the State, anyone with Internet access should have basic knowledge of information security.
In today’s world context, nations are mobilizing to reorganize their activities, norms, policies and strategies for cyber security and defense. However, it must be made clear that there is a subtle difference between the two terms. As explained earlier, cyber security concerns the protection of information. On the other hand, cyber defense also deals with the offensive and exploratory actions, which aim respectively to cause damage to the opponent and to gather information about the opponent.
It is in cyber defense that intentional threats like crime, terrorism, and sabotage are more connoted. For this reason, Nations legitimize themselves through the creation and structuring of cyber defense bodies. These organizations are present in large public and / or private institutions through network incident treatment centers, where they analyze the cybernetic traces left by various types of attacks and measure the impact caused in order to restrain future attacks and, Even, prepare cybernetic countermeasures.
Through the interoperability of Information Technology media, as well as its complexity and proliferation, it is evident the great importance of Cyber Defense today, which can be seen in two ways: from public-private and military sectors.
Unlike in the past, when a large amount of financial resources was spent during a battle between two nations, it is now possible to witness various cyber conflicts in which not a fraction of that amount is spent. It is precisely for this reason that developed countries are taking seriously the creation of large cyber defense centers, coordinated by military or even public and private institutions.
Cyber defense has been evolving and adapting to technological innovations and has been applied in three types of offensive or exploratory actions:
A) Social: focuses on specific techniques of social engineering, which may include the elaboration of malware, in which the victim is induced to provide information that can be used without authorization;
B) Sophisticated: performed by exploiting vulnerabilities, backdoors or through theft and use of valid access credentials;
C) Discrete: actions that are difficult to detect due to the realization of discrete or hidden movements so that the record of the attacks is mixed with the legitimate records generated.
The Importance of Cyber Security and Cyber Defense
Countries with little recent tradition of involvement in armed conflict tend to place little emphasis on national security. In the same way, several nations neglect cyber security, believing they are not potential targets.
However, security incidents that are constantly reported against public agencies, private institutions, and the general public that, depending on the scale and target, may even be considered terrorist acts, reflect how misplaced this position is.
During the Cold War, the United States and the Soviet Union made extremely forceful demonstrations of power, but they avoided direct confrontation at any cost, fearing the proportions and consequences of the Frankish strike. Currently, only this time in cyber space, it is possible to witness what could be called a virtual cold war, in which those involved carry out cyber attacks without assuming its authorship.
To further aggravate this scenario, it is also possible to see several aspects of organized crime in action, making it necessary to implement cyber security actions, which can be adopted in isolation or in combination:
A) Preventive: how actions of hardening, equipment exchange, programming improvement are applied in order to avoid or restrain the presence of cyber threats in the information assets;
B) Reactive: how actions are applied to correct a vulnerability exploited by a cybernetic threat.
The preventive actions in Cyber Security are important, because through them one tries to avoid or to minimize the threats, being able to be achieved by means of several techniques like: vulnerability evaluation, configurations of security parameters, support anti-malware, restriction to the sharing of information , Support between systems, awareness, training and exercises.
Reactive actions are essential for Cyber Security, since it is through them that incident response and intrusion detection services are implemented, along with content verification and forensic computing, which is responsible for the analysis of all traces and records Related to an incident, enabling the preservation, collection, processing and analysis of cybernetic traces.
CONCLUSION
Introducing the concepts of cyber security and defense, whether or not involved in the possibility of cyberwarfare, it is quite clear that we live in a world of growing threats that make the issue a global problem that involves urgent stakeholder action, Or creating entities specialized in supervision and control.
This world scale suggests that it will take a lot of effort to rewrite the rules that will govern cyberspace and the emergence of diverse strategic partnerships to act in the cyber world. In addition, the demand for skills related to Forensic Computing tends to grow more and more, because, in a highly connected world, it is inevitable that one has a large amount of cybernetic traces.
REFERENCES
ABNT. ISO / IEC 27037: 2013 Information technology – Security techniques – Guidelines for identification, collection, acquisition and preservation of digital evidence. Brazil: 2013.
CLARKE, Richard A., Knake, Robert K. Cyber War: The Next Threat to National Security and What To Do About It, HarperCollins Publishers, 2010.
FRANCO, Deivison Pinheiro. Segurança e Defesa Cibernética. In: VELHO, Jesus Antônio (org.). Tratado de Computação Forense. São Paulo: Millennium, 2016. Pp. 535-562.
GJELTEN, Tom. Cyberattacks, Terrorism Top U.S. Security Threat Report. Available in: <http://www.npr.org/2013/03/12/174135800/cyber-attacks-terrorism-top-u-s-security-threat-report>. Access in December 23, 2016.
IASIELLO, Emilio. Are cyber weapons effective military tools? Available in: <http://www.inss.org.il/uploadImages/systemFiles/2_Iasiello.pdf>. Access in December 23, 2016.
LIMA, Paulo. M. F. Computer Crimes and Computer Security. São Paulo: Atlas 2011.
SCHMITT. Michael. Tallinn manual on the international law applicable to cyber warfare. Available in: <http://www.peacepalacelibrary.nl/ebooks/files/356296245.pdf>. Access in December 23, 2016.
- Whitehouse. Executive Order. Available in: <https://www.whitehouse.gov/the-press-office/2015/04/01/executive-order-blocking-property-certain-persons-engaging-significant-m>. Access in December 23, 2016.
- Whitehouse. International Strategy for Cyberspace. Available in:<https://www.whitehouse.gov/sites/default/files/rss_viewer/International_Strategy_Cyberspace_Factsheet.pdf>. Access in December 23, 2016.
WENDT, Emerson and JORGE, Higor Vinicius Nogueira. Cyber Crimes – Threats and Investigation Procedures. 2nd Edition. Rio de Janeiro: Brasport, 2013.
WILSON, Clay. Cyber weapons: 4 defining characteristics. Available in: <https://gcn.com/articles/2015/06/04/cyber-weapon.aspx>. Access in December 23, 2016.
[1] http://www.digitalattackmap.com/
[3] https://cybermap.kaspersky.com/widget/
[4] http://threatmap.fortiguard.com/
[5] https://www.fireeye.com/cyber-map/threat-map.html
[6] http://www.zerodayinitiative.com/
[8] https://www.mitnicksecurity.com/S=0/shopping/absolute-zero-day-exploit-exchange
ABOUT THE AUTHOR
Deivison Pinheiro Franco
Graduated in Data Processing. Specialist in Computer Networks, in Computer Networks Support and in Forensic Sciences (Emphasis in Forensic Computing). Master in Computer Science and in Business Administration. Senior Security Analyst of Bank of Amazônia. University Professor. Computer Forensics Expert. Computer Forensics and Information Security Researcher and Consultant. IT Auditor and Penetration Tester. Member of the IEEE Information Forensics and Security Technical Committee. Member of the Brazilian Society of Forensic Sciences. C|EH, C|HFI, DSFE and ISO 27002 Senior Manager.
Mestre em Ciência da Computação e em Inovação Tecnológica; Especialista em Ciências Forenses, em Suporte a Redes de Computadores e em Redes de Computadores; Graduado em Processamento de Dados; Técnico Científico de TI – Analista Sênior do Banco da Amazônia; Professor de graduações e pós-graduações; Perito Judicial em Forense Computacional, Auditor de TI e Pentester; Membro do IEEE Information Forensics and Security Technical Committee; Membro da Sociedade Brasileira de Ciências Forenses; Colunista das Revistas Segurança Digital, Hakin9 e eForensics Magazine; CEH, CHFI, DSFE e ISO 27002 Advanced. Colunista do CryptoID
Leia aqui outros artigos escritos por Deivison Franco
