‘CryptoRom’ Crypto Scam Abusing iPhone Features to Target Mobile Users
22 de março de 2022Cybersecurity company Sophos, which has named the organized crime campaign “CryptoRom,” characterized it as a wide-ranging global scam
For Ravie Lakshmanan
Social engineering attacks leveraging a combination of romantic lures and cryptocurrency fraud have been deceiving unsuspecting victims into installing fake apps by taking advantage of legitimate iOS features like TestFlight and Web Clips.
Cybersecurity company Sophos, which has named the organized crime campaign “CryptoRom,” characterized it as a wide-ranging global scam.
“This style of cyber-fraud, known as sha zhu pan (杀猪盘) — literally ‘pig butchering plate’ — is a well-organized, syndicated scam operation that uses a combination of often romance-centered social engineering and fraudulent financial applications and websites to ensnare victims and steal their savings after gaining their confidence,” Sophos analyst Jagadeesh Chandraiah said in a report published last week.
The campaign works by approaching potential targets through dating apps like Bumble, Tinder, Facebook Dating, and Grindr, before moving the conversation to messaging apps such as WhatsApp and urging the victims to install a cryptocurrency trading application that’s designed to mimic popular brands and lock people out of their accounts and freeze their funds.

Previous variants of the social engineering scam observed in October 2021 were found to leverage lookalike App Store pages to deceive people into installing the rogue iOS apps, not to mention abuse Apple’s Developer Enterprise Program to deploy sketchy mobile provisioning profiles to distribute the malware.
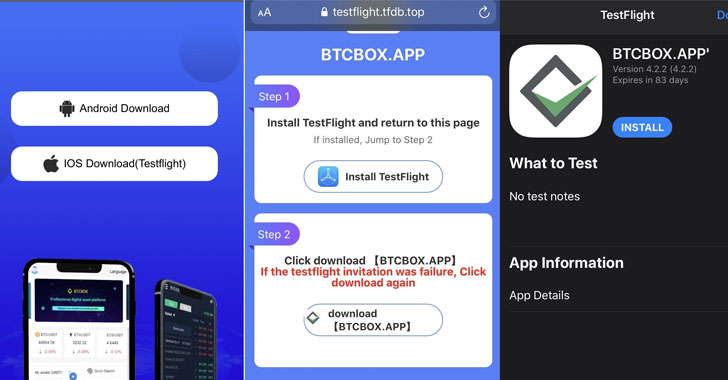
But the new attack wave observed by Sophos takes advantage of Apple’s TestFlight beta testing framework and a device management feature called Web Clips, which allows URLs to specific web pages to be placed on the home screen of users’ iOS devices just like a traditional application.
Once installed, the crooks promise the individuals huge financial returns in return for making a monetary investment, while artificially manipulating the numbers on the fake app to “reinforce the con” and convince the victims into believing that “they are making money” through the platform.
“The scam doesn’t end with just fooling victims into investing,” Chandraiah elaborated. “When victims try to withdraw funds from their big ‘profit,’ the crooks use the app to inform them that they need to pay a ‘tax’ of 20% of their profits before funds can be withdrawn — and threaten that all their investments will be confiscated by tax authorities if they do not pay.”
Source: The Hacker News
INTERNATIONAL NEWS
Crypto ID publishes international articles about information security, digital transformation, cyber security, encryption and related topics.
Please check here!
Facial recognition for travel and onboarding top this week’s biometrics and digital ID news
Symantec Connects 40 Cyber Attacks to CIA Hacking Tools Exposed by Wikileaks




